Unleashing the Power of Protection: Why Network Access Controls are Vital for Data Security

Safeguarding Data in the Digital Jungle
In today’s fast-paced digital world, where information flows freely and cyber threats lurk around every corner, organizations must fortify their data defenses. The need to protect sensitive information has become more critical than ever before. In this age of technological marvels, implementing robust network access controls has emerged as the key to ensuring the safety of valuable data. Join us as we explore why organizations worldwide are turning to these safeguards to shield their digital assets from harm.
The Importance of Network Access Controls
The Rise of Digital Vulnerabilities
With the proliferation of cloud computing, Internet of Things (IoT) devices, and remote working practices, organizations face an expanding attack surface. Malicious actors are constantly devising innovative methods to breach network defenses and gain unauthorized access to sensitive data. This evolving landscape demands a proactive approach to security, where network access controls play a pivotal role.
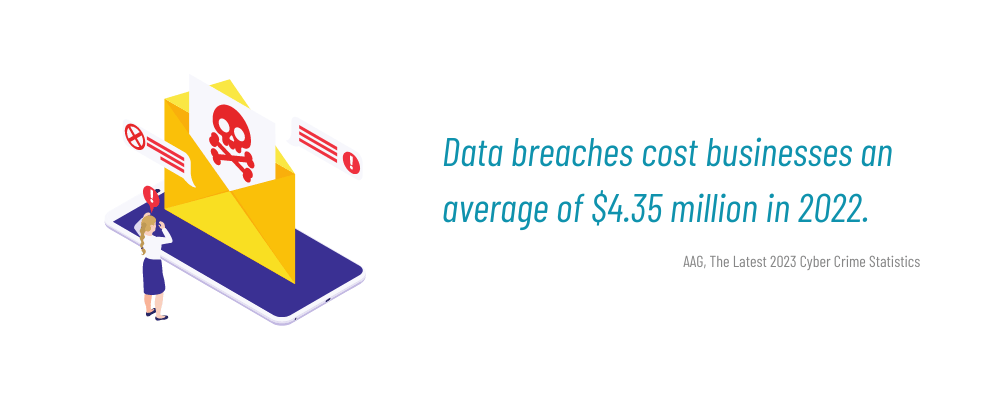
Fortifying the Perimeter
Network access controls act as sentinels, standing guard at the gates of an organization’s digital infrastructure. By defining and enforcing access policies, these controls ensure that only authorized personnel can enter the network. Whether it’s a virtual private network (VPN) for remote access or an authentication system for employees, these controls create a fortified perimeter that prevents unauthorized entry.
Granular Control, Enhanced Security
One of the significant advantages of network access controls is their ability to provide granular control over user access. Through user authentication, multi-factor authentication (MFA), and role-based access controls (RBAC), organizations can restrict access to specific resources, limit privileges, and reduce the risk of data breaches. By granting the right people the right level of access, organizations can maintain the delicate balance between security and operational efficiency.
Defense in Depth
In an era where a single breach can lead to disastrous consequences, organizations must adopt a layered defense strategy. Network access controls complement other security measures, such as firewalls, intrusion detection systems, and encryption. By adding an additional layer of protection, these controls fortify the overall security posture of an organization, making it harder for attackers to penetrate the network perimeter.
Regulatory Compliance
As data privacy regulations continue to evolve worldwide, organizations must demonstrate compliance with stringent standards. Network access controls play a vital role in meeting these requirements. By implementing robust access controls and audit trails, organizations can showcase their commitment to data protection, ensuring that they are in line with regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA).
Safeguarding Business Continuity
The impact of a data breach can be catastrophic, leading to reputational damage, financial loss, and disrupted operations. By implementing network access controls, organizations can minimize the risk of unauthorized access and mitigate the potential fallout of a security incident. Protecting data not only safeguards an organization’s operations but also fosters trust among customers, partners, and stakeholders.
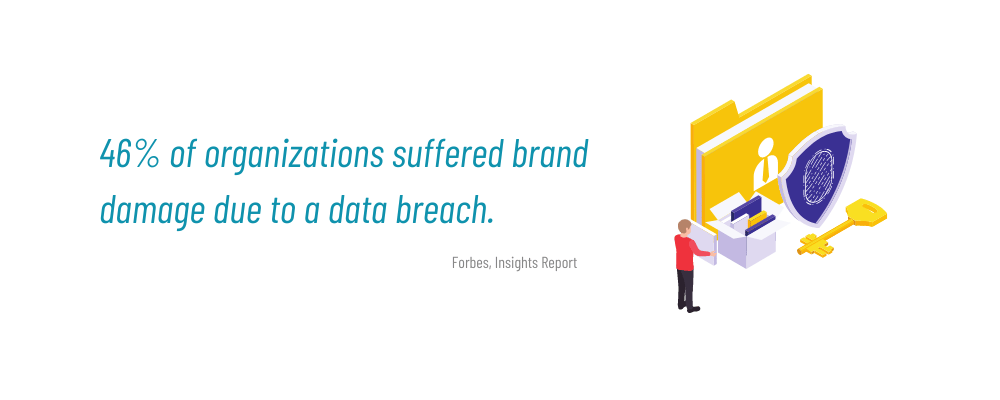
Preservation Requires Network Access Controls
In the digital era, where data is the lifeblood of organizations, protecting sensitive information has become paramount. Implementing network access controls serves as a robust line of defense against cyber threats, ensuring that only authorized individuals can access valuable data. By fortifying the network perimeter, providing granular control, and adhering to regulatory compliance, organizations can safeguard their digital assets and preserve their reputation. So, don’t wait—unleash the power of protection with network access controls and embark on a secure digital journey where your data is shielded from the ever-present threats of the digital jungle.
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!