One of the worst things you can go through as a company is a data breach. It costs a small fortune (average of $4.35 million as of 2022), destroys your reputation, often leads to bankruptcy, and takes a massive toll on your employee’s well-being. Thus, preventing a data breach should be top of your to-do list. Today, that means taking a hard look at your connected endpoints – starting with IoT – and making sure you have the necessary tools to keep them from putting you at risk.
Safety Third for IoT
IoT (Internet of Things) is loosely defined as devices other than computers and networking equipment that connect to the internet, and these days that is just about everything. There are currently over 13 billion IoT things connected around the globe, with that number projected to grow two-fold to 25.4 billion by 2030.

The unfortunate reality of these billions of devices is that they are not designed with security at the top of the list…if it’s even on the list. Default administrator passwords, security patches that are slow to be released if at all, and impossible to update firmware are some of the many ways IoT devices make your network vulnerable.
Behold, IoT Fingerprinting!
One of the trickiest things about IoT devices is just figuring out that they’re there. IoT devices prioritize ease of setup and use (most of them just connect to the internet and away you go) over best security practices, which makes them an attractive target for hackers. They don’t respond to SNMP, WMI, or other common monitoring protocols, and they typically run locked-down operating systems that don’t allow for additional software like agents. It’s easy for them to hide in plain sight, just waiting to be exploited.
This is where IoT fingerprinting comes in – a good option here is a NAC solution that has the ability to pull information from IoT devices to give you critical information like operating system, manufacturer, and firmware version. There are several ways to get this information with various levels of accuracy – Nmap scanning, DHCP, NetFlow, MAC address look up, etc. Many of these options require additional configurations or features in your network, so it’s important to pick one that will work with what you already have without creating any network latency.
Staying in Your IoT Lane
In 2017, a casino was hacked using a fish tank as an entry point. Two buildings in Finland had their heat turned off in November through a DDoS attack on the internet-connected thermostats (and with the average temperature just a bit above freezing, that put some lives at risk.). When security startup Verkada was breached, hackers got access to not only the live camera feeds, but archived security camera footage from Tesla, Equinox, Cloudflare, and others.
One of the most important ways to protect your networks is making sure they are segmented – the practice of separating your network into different VLANs with limited access to specific resources. This is particularly important for your IoT devices because if they are breached, you don’t want the hackers to be able to move through your network and cause further damage. Ideally you would create a special IoT VLAN that had internet access only, and then use a security tool like a NAC to automatically move all of your IoT devices to that specific VLAN.
After all, your fish tank probably does not need access to your customer database.
Spoof Proof IoT
When it walks like a duck, but barks like a dog….
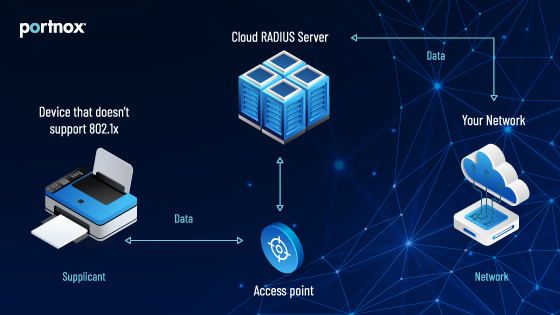
One challenge in adding IoT devices onto your network is the fact they don’t support 802.1x authentication. That means they need to bypass your usual safeguards and get on some other way.
MAC Authentication Bypass (MAB) is a way for a device to authenticate based on its MAC address, rather than any kind of certificate or identity provider. Essentially, a device connects to a switch or wireless access point and then does not respond to requests for 802.1x authentication (because it can’t). The device then sends a packet containing its MAC address to the switch, which forwards it onto the RADIUS server and determines if it gets access or not.
Obviously, the issue here is that there is no real authentication happening, so you need something to ensure you’re not just letting every device onto your network. The most common way to do this is to set up a MAC address filter, which your RADIUS server will then use to validate that the device asking for access is allowed, but that’s still not a great solution because MAC addresses can be spoofed.
Spoofing is, in fact, laughably easy – a quick Google search yields over 6 million how-to results! To prevent a potential bad actor from gaining access, you want to make sure you have a solution that can do some kind of comparison between a device’s past behavior and present behavior so that if a security camera suddenly starts behaving like a laptop, you can remove it from the network.
If all this seems a bit overwhelming, well, securing IoT can definitely be a big undertaking.
IoT Device Trust
Thankfully, there are tools in the zero trust security space that have recognized how important it is to keep these devices secure and can do most of the heavy lifting for you. Portnox combines all of these features – fingerprinting, access control, and secure MAB, into a collection called IoT Device Trust. These features are key to keeping your network secure no matter how many things live on your internet.