How NAC Supports SOC 2 Compliance

Achieving SOC 2 compliance is crucial for any company that wants to show they have a strong commitment to cybersecurity and assure their customers that they are taking smart steps to prevent a data breach.. NAC (Network Access Control) software plays a critical role in helping achieve SOC 2 certification.
SOC 2 (System and Organization Controls) was developed by the American Institute of Certified Public Accountants and is the name of a suite of reports produced during an audit. These reports focus on internal controls across five Trust Service Criteria: Security, Availability, Processing Integrity, and Confidentiality.
What is Network Access Control?
Network Access Control (NAC) is a security solution that enforces policy compliance on devices that attempt to access network resources. NAC can deny network entry, restrict access to certain areas, or place devices in a quarantined area until they meet the network’s security standards. This mechanism is vital in preventing unauthorized access and managing the security of devices over their lifecycle.
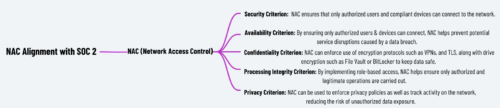
How NAC aligns with SOC2:
1. Enhancing Security (Security Criterion)
- Access Control: NAC ensures that only authorized users and devices can connect to the network, reducing the risk of unauthorized access. It enforces policies that control who has access to what resources based on user roles, device types, and compliance with security policies.
- Endpoint Security: NAC can check devices for compliance with security policies before they are allowed access. This includes checking for up-to-date antivirus software, patches, and other security configurations, ensuring that only secure and compliant devices can connect to the network.
- Segmentation: NAC can enforce network segmentation by restricting access to sensitive areas of the network based on user roles or device types. This helps protect critical data from unauthorized access and reduces the risk of lateral movement in the event of a breach.
2. Ensuring Availability (Availability Criterion)
- Network Stability: By ensuring that only authorized and compliant devices can connect to the network, NAC helps prevent potential disruptions caused by insecure or compromised devices, thus maintaining the availability of network resources.
- Policy Enforcement: NAC can help enforce bandwidth management policies, ensuring that critical applications and services remain available and are not disrupted by unauthorized or non-essential traffic.
3. Maintaining Confidentiality (Confidentiality Criterion)
- Data Protection: NAC helps protect sensitive and confidential data by ensuring that only authorized users and devices can access networks and systems where this data is stored or processed. It can restrict access to certain network segments or applications based on the confidentiality level of the data.
- Encryption Enforcement: NAC can enforce the use of secure communication protocols (such as VPNs or TLS) for devices accessing sensitive data, ensuring that data in transit is protected from interception or unauthorized access.
4. Monitoring and Auditing (Supporting Multiple Criteria)
- Audit Trails: NAC solutions typically include detailed logging and monitoring capabilities, which are essential for creating audit trails. These logs help demonstrate compliance with SOC 2 by providing evidence of access controls, policy enforcement, and network activity.
- Real-time Monitoring: NAC provides real-time visibility into who is accessing the network and how, which helps in detecting and responding to security incidents quickly, an essential aspect of maintaining compliance with SOC 2.
5. Supporting Processing Integrity (Processing Integrity Criterion)
- Ensuring Accurate Data Processing: By controlling and monitoring which devices and users can access processing systems, NAC helps ensure that only authorized and legitimate operations are carried out. This reduces the risk of errors or unauthorized processing activities.
6. Privacy (Privacy Criterion)
- User and Device Identification: NAC can be used to enforce privacy policies by ensuring that only authenticated and authorized users can access personal data. It can also track and control how data is accessed, aligning with privacy requirements and reducing the risk of unauthorized data exposure.
Benefits of Implementing NAC in Alignment with SOC 2
Implementing NAC not only supports compliance with SOC 2 but also brings several benefits to organizational cybersecurity strategies:
- Enhanced Visibility and Control: NAC provides complete visibility of all devices on the network, including BYOD and guest devices, allowing for better control of who accesses what resources.
- Automated Response: NAC can automatically respond to non-compliance and security threats by restricting access or quarantining devices, thus reducing the risk of security breaches.
- Regulatory Compliance: For organizations subject to regulations, NAC helps in maintaining continuous compliance with security policies and regulations.
Implementing NAC in alignment with SOC 2 compliance demonstrates a commitment to cybersecurity. It provides a comprehensive approach to securing network access, protecting sensitive data, and maintaining the integrity and availability of network resources. Not only does it help organizations meet the stringent requirements of SOC 2 but also enhances operational efficiency and customer trust, providing a solid foundation for long-term business success.
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!



