How NAC Supports NIST SP 800-53 Cybersecurity Requirements

In the ever-evolving landscape of cybersecurity, organizations continuously seek robust mechanisms to protect their networks and data. One effective approach is implementing Network Access Control (NAC), which plays a critical role in meeting the stringent cybersecurity requirements set forth by the National Institute of Standards and Technology (NIST) in its Special Publication 800-53. This publication provides a catalog of security and privacy controls for federal information systems and organizations to enhance their security posture.
What is Network Access Control?
Network Access Control (NAC) is a security solution that enforces policy compliance on devices that attempt to access network resources. NAC can deny network entry, restrict access to certain areas, or place devices in a quarantined area until they meet the network’s security standards. This mechanism is vital in preventing unauthorized access and managing the security of devices over their lifecycle.
Alignment of NAC with NIST SP 800-53
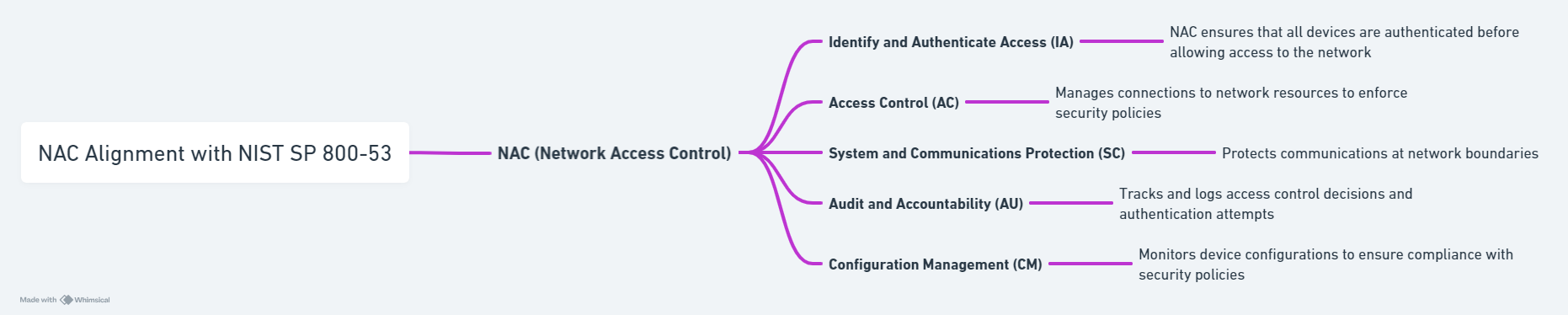
NAC supports several key security controls outlined in NIST SP 800-53, ensuring that organizational networks remain secure and resilient against threats. Here’s how NAC aligns with some of these controls:
1. Access Control (AC)
NAC systems are paramount in enforcing access control policies by ensuring that only authenticated and authorized devices can access network resources. This is in line with AC-3 (Access Enforcement) and AC-17 (Remote Access), which mandate that access to organizational systems is controlled and managed effectively.
2. Identification and Authentication (IA)
By integrating with identity management solutions, NAC ensures that all devices are properly identified and authenticated before gaining network access, aligning with IA-2 (Identification and Authentication). This prevents unauthorized devices from accessing sensitive data and systems.
3. System and Communications Protection (SC)
NAC contributes to the protection of system boundaries through policies that isolate and control the flow of information between networks. SC controls, such as SC-7 (Boundary Protection), are supported by NAC solutions that monitor and control communications at the boundaries of network segments.
4. Audit and Accountability (AU)
NAC systems can log and monitor all attempts to access the network, providing a detailed account of device activities. This supports AU-2 (Audit Events) and AU-12 (Audit Generation) requirements by ensuring that actions affecting security are recorded and available for review.
5. Configuration Management (CM)
NAC aids in maintaining the security configuration of devices throughout their lifecycle. By ensuring devices comply with CM-7 (Least Functionality), NAC restricts software installations and functions that might compromise security.
Benefits of Implementing NAC in Alignment with NIST SP 800-53
Implementing NAC not only supports compliance with NIST SP 800-53 but also brings several benefits to organizational cybersecurity strategies:
- Enhanced Visibility and Control: NAC provides complete visibility of all devices on the network, including BYOD and guest devices, allowing for better control of who accesses what resources.
- Automated Response: NAC can automatically respond to non-compliance and security threats by restricting access or quarantining devices, thus reducing the risk of security breaches.
- Regulatory Compliance: For organizations subject to regulations, NAC helps in maintaining continuous compliance with security policies and regulations.
The alignment of Network Access Control with NIST SP 800-53 requirements is a testament to its value in a comprehensive cybersecurity strategy. By enforcing robust access control, ensuring proper identification and authentication, and supporting system integrity and accountability, NAC not only adheres to but enhances the security controls recommended by NIST. As cyber threats continue to evolve, the role of NAC in securing network environments remains indispensable, ensuring that organizations can protect their critical information assets effectively.
Try Portnox Cloud for Free Today
Gain access to all of Portnox's powerful zero trust access control free capabilities for 30 days!